零信任范式的采用

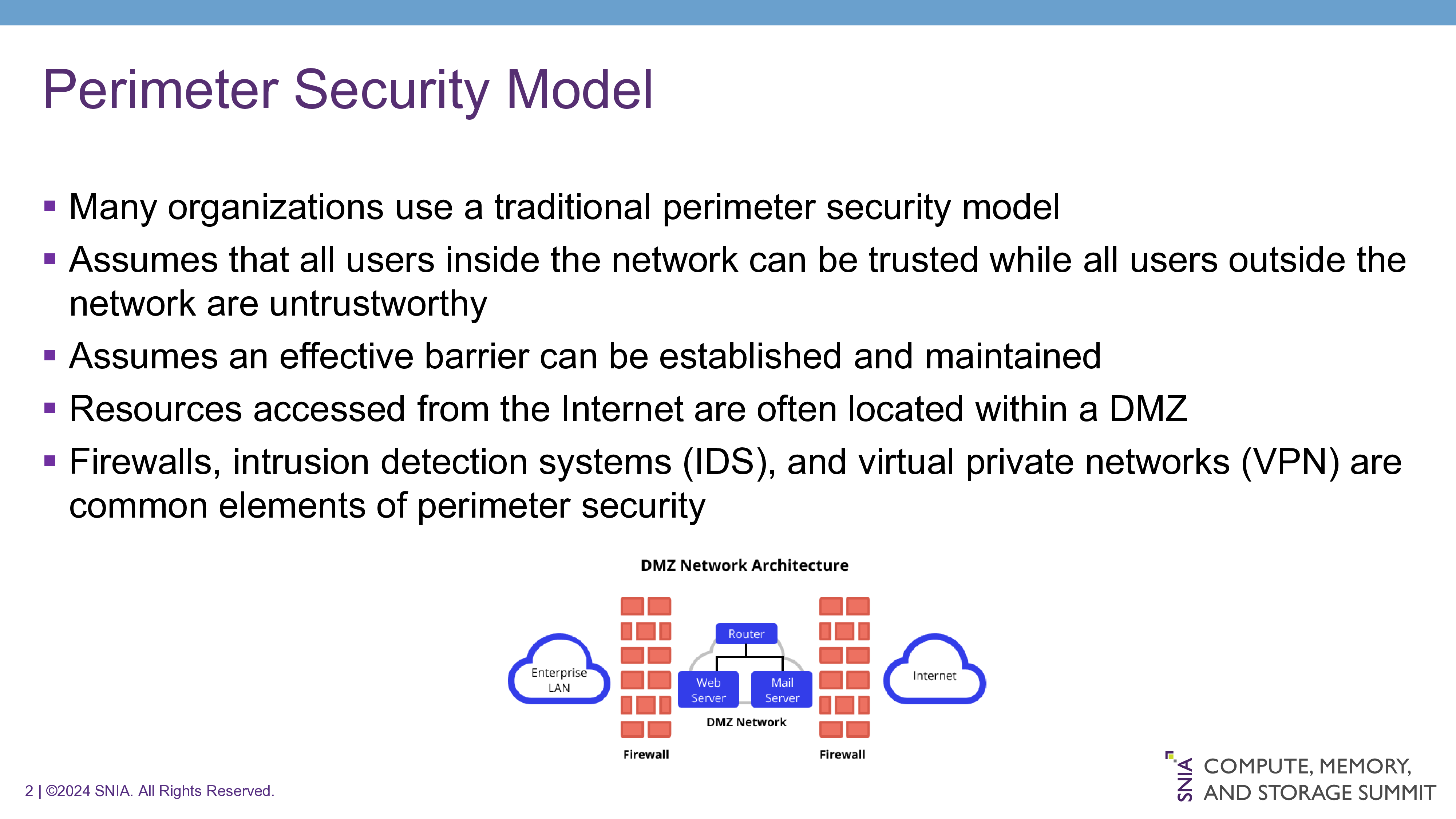

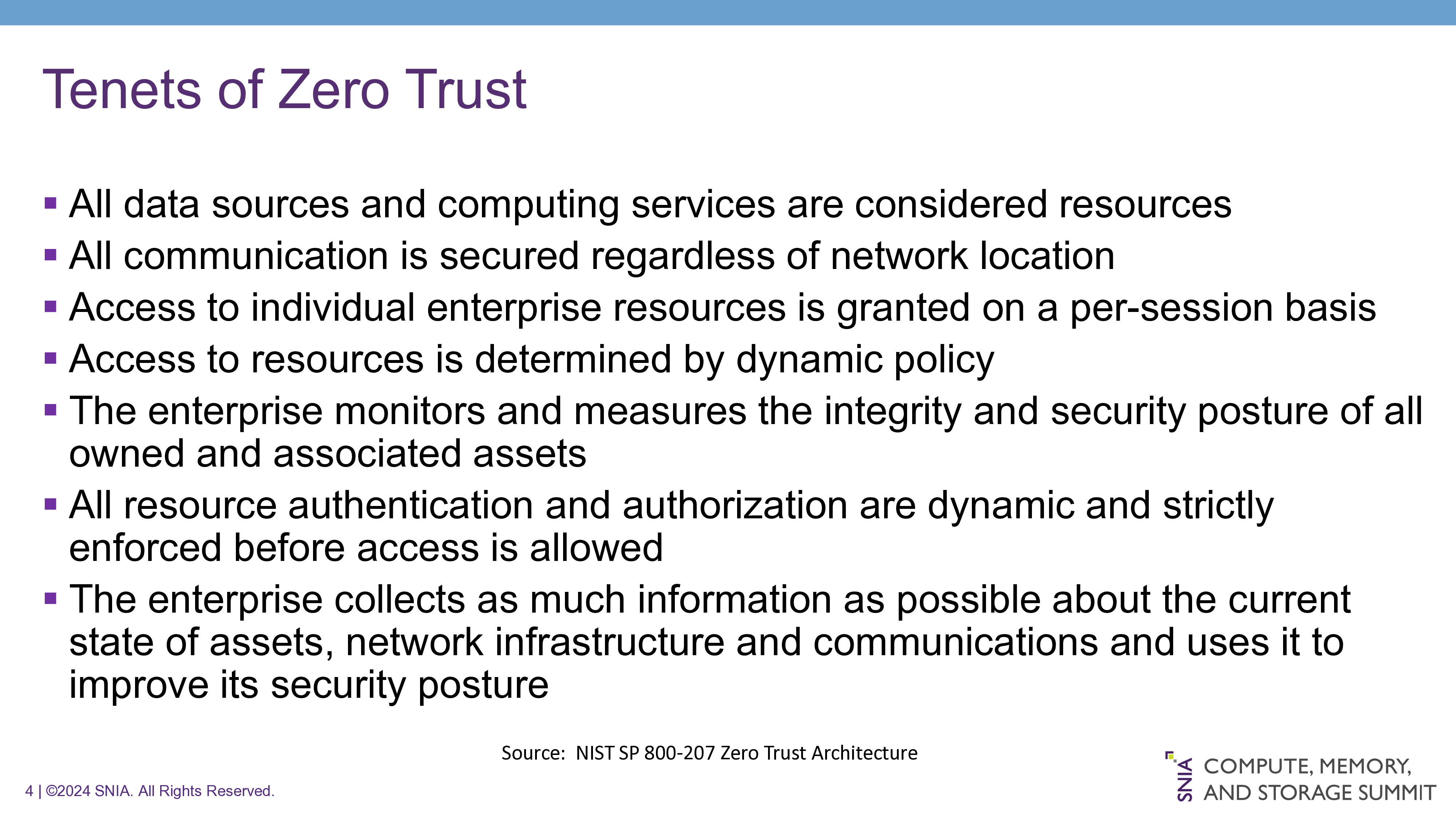

1| ©2024 SNIA. All Rights Reserved. Adopting the Zero Trust ParadigmEric Hibbard, CISSP, FIP, CISASamsung Semiconductor, Inc.2 | ©2024 SNIA. All Rights Reserved. Perimeter Security ModelMany organizations use a traditional perimeter security modelAssumes that all users inside the network can be trusted while all users outside the network are untrustworthyAssumes an effective barrier can be established and maintainedResources accessed from the Internet are often located within a DMZFirewalls, intrusion detection systems (IDS), and virtual private networks (VPN) are common elements of perimeter security3 | ©2024 SNIA. All Rights Reserved. Zero Trust (ZT) Security ModelPrimarily focused on data and service protection; can also includeall enterprise assets (devices, infrastructure components, applications, virtual and cloud components) subjects (end users, applications and other non-human entities that request information from resources)Assumes that an attacker is present in the e
相关推荐
相关内容
-

腾讯云中国信通院中国通信标准化协会2024年AI大模型应用发展研究报告58页
分类:
时间:2025-05-09
标签:
格式:PDF
-

利用智能视觉组件简化嵌入式视觉开发
分类:
时间:2025-05-09
标签:
格式:PDF
-

俄勒冈州交通规划在快速变化和不确定的时代利用情景规划的案例研究
分类:
时间:2025-05-09
标签:
格式:PDF
-

SiCMOSFET技术进展与发展方向
分类:
时间:2025-05-09
标签:
格式:PDF
-

康嘉种业-每一头猪都代表着康嘉人的尊严
分类:
时间:2025-05-09
标签:
格式:PDF
-

汽车行业周报小米SU7Ultra正式发布Helix带动Figure效率跃升-25030118页
分类:
时间:2025-05-09
标签:
格式:PDF
-

杨昕-AI驱动抖音用户体验中台探索与实践
分类:
时间:2025-05-10
标签:
格式:PDF
-

跨国的AI采用者的肖像公司特征资产的互补性和生产力
分类:
时间:2025-05-10
标签:
格式:PDF
-

OrChechikandDanielFrank-从侦察到毁灭揭露伊朗AgriusAPT最新TTPs
分类:
时间:2025-05-10
标签:
格式:PDF
-

爱立信混合工作模式调查结果
分类:
时间:2025-05-10
标签:
格式:PDF















